Authentication Bypass in Fortinet Products Enables Unauthorized FortiCloud SSO Access

By Bryan Zatezalo | Cyber Threat Intelligence Analyst
Background Information
CVE-2025-59718, disclosed by Fortinet in December 2025, continues to be associated with active exploitation. Current reporting indicates that recent attack activity closely mirrors the exploitation patterns observed shortly after the vulnerability’s initial disclosure. Fortinet administrators have raised concerns regarding potential post-patch exploitation, and multiple third-party security providers have independently reported evidence suggesting the vulnerability may still be leveraged in the wild.
Current Vulnerability Picture
The flaw allows an attacker to bypass single sign-on (SSO) authentication by leveraging maliciously crafted SAML messages when FortiCloud SSO functionality is enabled. This vulnerability is estimated to impact approximately 11,000 devices with FortiCloud SSO enabled. Observed attacker activity includes post-compromise configuration changes and data exfiltration on affected devices, indicating active exploitation beyond initial access. In the most recent update directly from FortiGuard as of 2026-01-27, the Forticloud SSO on the FortiCloud side is unsupported from devices running vulnerable versions. A full list of the version and effects is in the sources at the end of this bulletin.
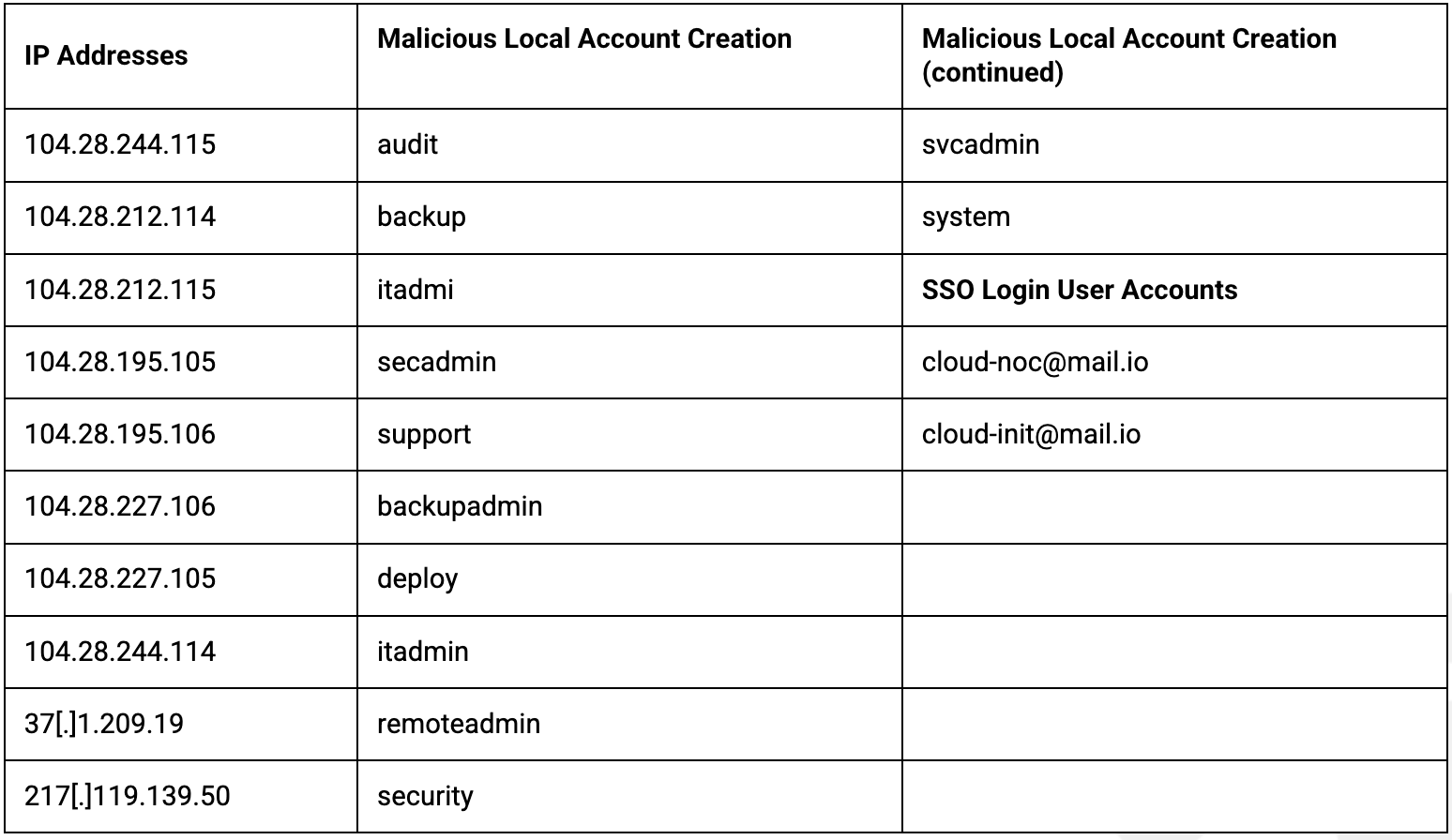
Indicators of Compromise
Below are listed Indicators of Compromise from FortiGuard Labs:
Recommendations
Recommendations include standard security best practices such as ensuring all FortiGate devices are fully up to date with the latest patches. As an additional protective measure, organizations may temporarily disable the “Allow Administrative Login using FortiCloud SSO” setting. Doing so prevents attackers from exploiting this vulnerability by removing the affected authentication pathway. However, this change may require the implementation of additional security controls to ensure alternative administrative login methods remain adequately protected.
Conclusion
In conclusion, malicious threat actors seeking access to sensitive systems and data are not limited to novel or previously unknown attack vectors. While ensuring devices are fully patched and up to date significantly reduces risk, it does not fully eliminate the possibility of exploitation. Ostra Security continues to monitor evolving threats through AI-assisted analysis, continuously updated detection rules, and ongoing intelligence correlation to identify suspicious activity that may persist even after remediation efforts. This layered approach helps ensure that emerging and residual risks are detected and addressed in a timely manner.
Sources:


.png)
.png)